Abnormal Blog
Keep up with the latest news in cybersecurity with insight from our team of experts.
Facebook phishing attacks are popular because users tend to use the same email address and password for other sites. In this attack, the cybercriminal impersonates Facebook to send out a phishing attack using a legitimate Facebook link.
For SOC analysts, managing an employee-reported phishing mailbox can be a double-edged sword. On one hand, legacy tools have made it easy for employees to report would-be business email compromise (BEC) and credential phishing emails. On the other hand...
Although tax season has passed, IRS impersonation scams persist, putting many Americans at risk for identity theft and payment fraud. In this attack, scammers impersonate the IRS by sending out a fake tax form to collect valuable personal and financial information.
Threat researchers at Abnormal Security recently discovered a coordinated spear-phishing campaign targeting numerous enterprise organizations. The attackers compromised hundreds of legitimate accounts and are sending emails...
Quickbooks is popular accounting software that also supports the management of essential business functions such as payroll, billing, and invoicing. Its widespread use, especially among small businesses, has made it a target for impersonation...
With many employees forced to work from home because of COVID-19, cybercriminals can take advantage of the fear and uncertainty caused by the pandemic. This attack features a new phishing scheme around returning to the office. Despite (or perhaps because of) the rise in COVID-19...
On October 21st, 2020, just two weeks before the US general election, many voters in Florida received threatening emails purportedly from the “Proud Boys." These attacks often included some personal information like an address or phone number, threatened violence...
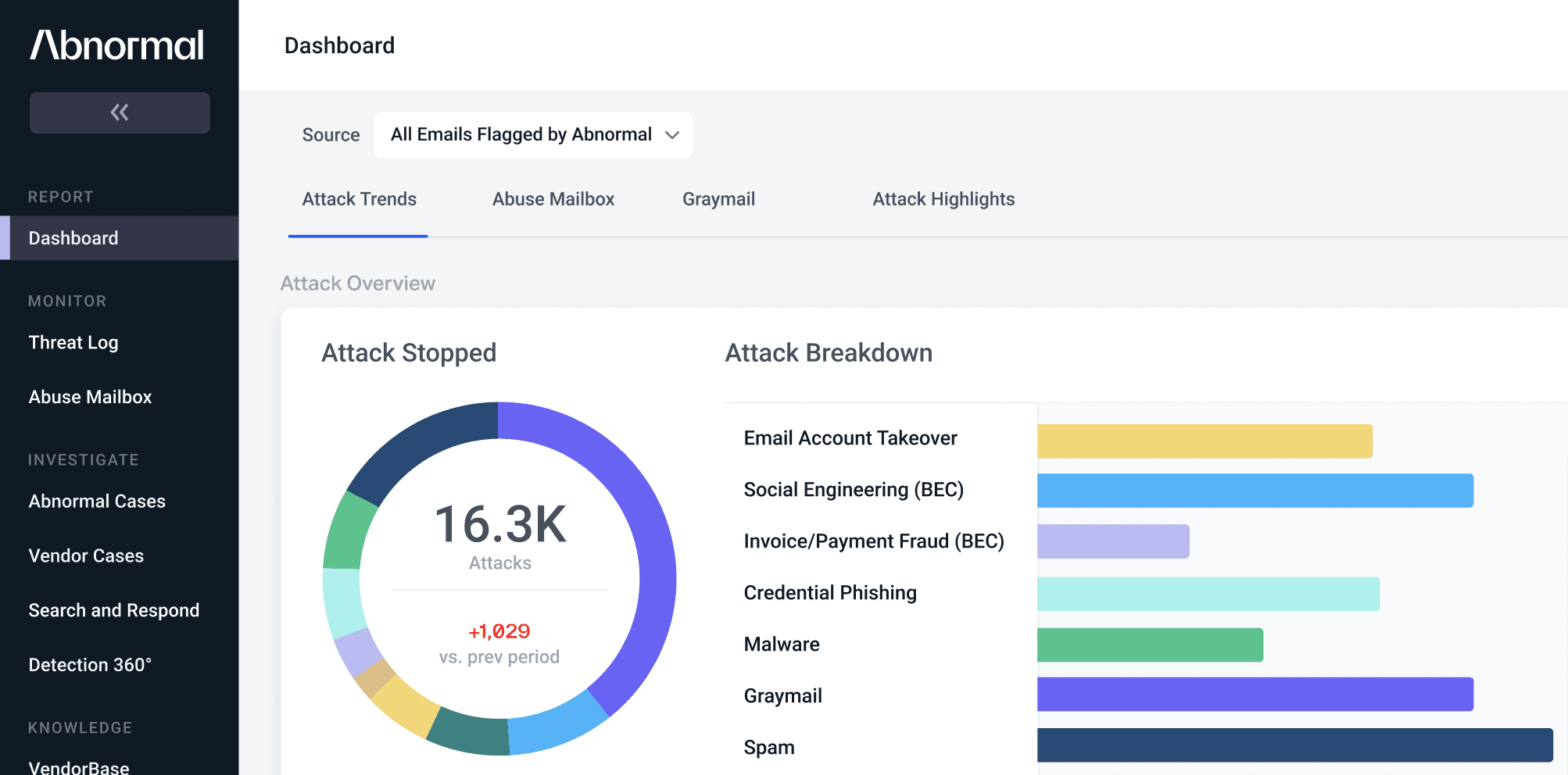
At Abnormal Security, one of our key objectives is to build a detection engine that can continuously adapt to a changing attack landscape. As such, we want to ensure that our systems can rapidly adjust to recent and high-value messages—even with...
When we founded Abnormal Security more than two and a half years ago, we met with 50 top CIOs and CISOs who told us two things: they needed a solution to stop a novel set of cyberattacks that increasingly bypassed legacy email security solutions, and they needed it...
Sophisticated social engineering email attacks are on the rise and getting more advanced every day. They prey on the trust we put in our business tools and social networks, especially when a message appears to be from someone on our contact list, or even...
A recent Amazon phone scam involves cybercriminals sending a fake email from Arnazon. Here's how we detected it.
Healthcare continues to be a preferred method for cyber attacks, and this attack features an impersonation of UnitedHealthcare in the form of a request for a claim. The email appears to originate from notifications@e-notifications.myuhc.com, which is an authorized...
Jesh Bratman, a founding member at Abnormal Security and Head of Machine Learning, was just featured on The Tech Trek’s podcast. Jesh deeps-dives into his past, building ML systems to detect abusive behavior at Twitter, and how he used this background to transition...
Recently, there has been a rise in scam emails demanding recipients to pay a ransom with bitcoin, or else the personal information attackers have gathered about the recipient will be released to the public. The means by which attackers have obtained this information...
Sending fraudulent purchase orders for goods and services is a common tactic attackers use to receive free merchandise. In this attack, attackers are impersonating the United States Transportation Command Office of Small Business Programs and sending an RFQ in...
When Abnormal Security was founded, our engineering and data science teams were focused on solving the toughest—and most expensive—email security problem for enterprises: business email compromise, or BEC. Fast-forward to today and Abnormal serves some of the largest enterprises...
As bitcoin and other cryptocurrencies become increasingly popular, attackers are taking advantage. This attack leverages bitcoin to fool early adopters of cryptocurrency with BTC Era into paying for what they believe is an investment, but is really a guise...
With unemployment on the rise, attackers are exploiting individuals in search of new positions. This method makes use of targeted social engineering techniques, combining email and mobile platforms, to reap information from victims. In this attack, malicious actors...
Compromised accounts are commonly used by cybercriminals to send additional attacks because they appear to originate from a trustworthy source—typically a known partner or customer, or a known coworker within the organization. In this attack, the account was first...
Abnormal recently detected campaigns targeting our customers where malicious actors will impersonate major brands and reach out to accounting teams to ask if there are any outstanding invoices for the company they are impersonating. Abnormal classifies these messages...
Skype is used prolifically in both casual and business settings. As a result of its affiliation with Microsoft, it is a popular choice for attackers to impersonate in order to trick victims into handing over their Microsoft credentials. In these attacks, the sender...
SharePoint is an increasingly popular tool for Microsoft users, especially in a time when millions of employees are working remotely. In this attack, malicious actors make use of an automated message from Sharepoint to send phishing emails. This attack...
Microsoft provides security alerts in the case of fraudulent logins on user accounts. Users are usually able to trust these emails due to the source being from a trusted brand. And because the email relates to account security, the recipient may unconsciously trust...
Microsoft Office offers one-time purchase and subscription plans and has numerous official resellers for its products. Scammers use this fact as an opportunity to impersonate Microsoft and their resellers in order to steal sensitive user data, as well as for...
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.