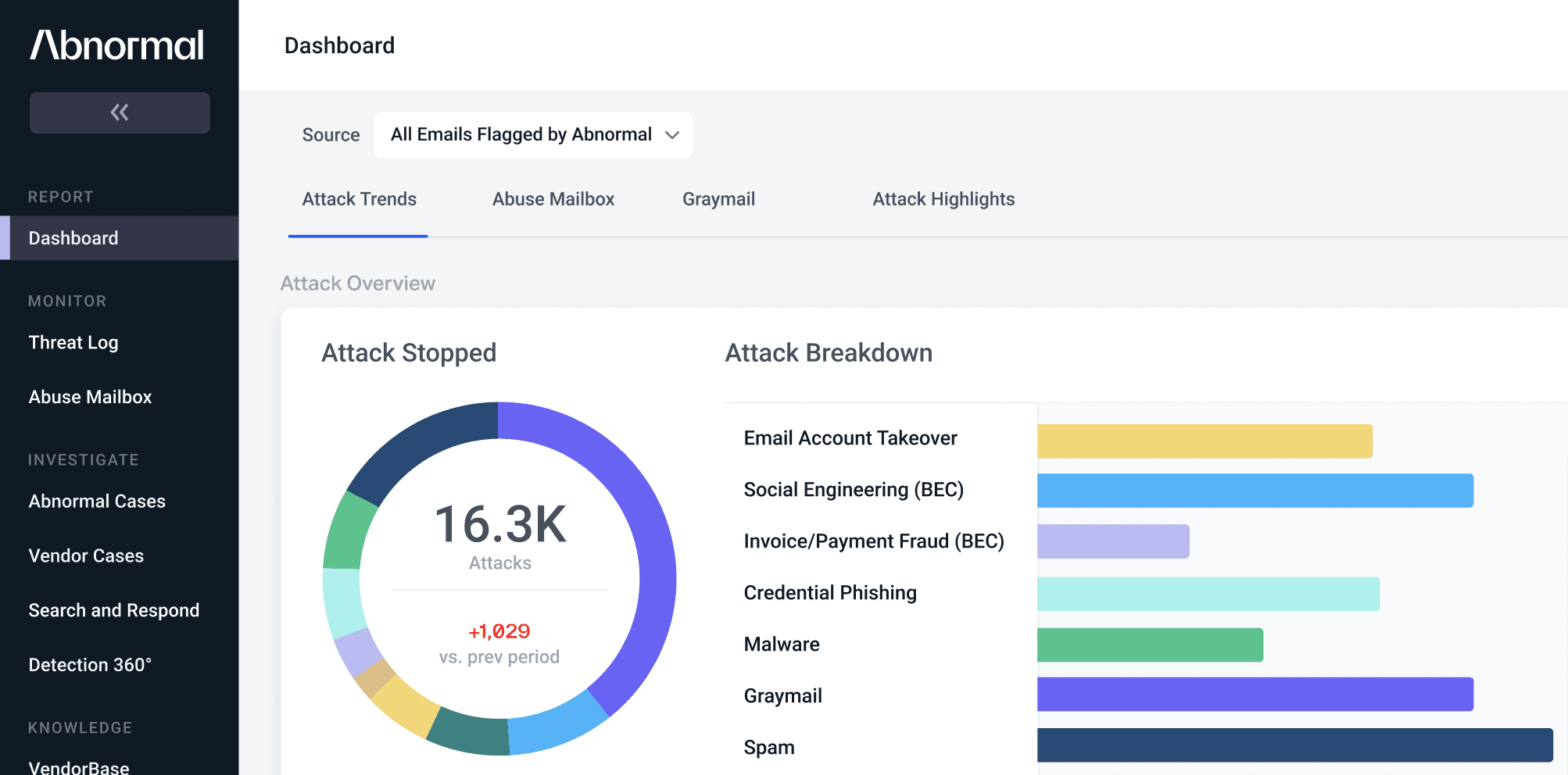
Extending Abnormal Protection and Visibility Across Cloud Platforms with AI
Cloud account compromise is the primary concern of security teams across the enterprise. This is evidenced by a survey we recently conducted, interviewing 300 security leaders and practitioners across all industries. While there are a variety of solutions available to defend against account takeovers and identity compromise, 86% of those same survey respondents noted current tools are inadequate at effectively stopping compromise.
Newsmaking breaches involving stolen credentials and compromised cloud identities like those attacks perpetrated by the Scattered Spider threat group reinforce this glaring security gap. Threat groups are buying session tokens for pennies on the Dark Web to hijack cloud accounts, socially engineering their way into privileged account access with messages written by generative AI tools, and bypassing MFA with as-a-service solutions sold on an inverse technology market that turns amateur criminals into nation-state caliber attackers.
To combat this evolving threat landscape, Abnormal is extending its cloud-native AI platform, seamlessly integrating with the cloud and SaaS applications your organization uses daily—transforming the way security teams monitor and protect cloud identities.
This expansion contains two distinct layers:
No-cost integration to cloud applications like Salesforce, Okta, and Amazon Web Services (AWS), providing unified visibility and cross-platform, single-click remediation.
A new product offering that leverages human behavior AI to do all the work of monitoring user activity across platforms, detecting signs of compromise, and automatically remediating accounts
Let’s unpack how these new capabilities protect beyond the inbox and stop the growing trend of cloud identity compromise.
Challenge #1: Visibility Into Notable Activity Across the Cloud
As mentioned in the introduction, cloud identity compromise is a growing threat, but before even addressing this threat, security teams must address the cloud visibility gap by:
Gaining direct access and visibility into user behaviors across cloud and SaaS applications. Security teams are tasked with protecting these applications but are not the administrators, limiting access.
Consolidated view of cloud identities and the events and activities associated with those identities. An inability to do this efficiently hampers investigation.
Taking swift action to remediate threats across all platforms, ideally through a single click. Today, incident response can be fragmented across various tools, slowing remediation efforts.
Today, Abnormal integrates with your core cloud platforms—email and identity—to analyze user activity, detect behavioral anomalies, and build comprehensive profiles and identity genomes for each user in PeopleBase. While this provides tremendous value when investigating suspicious users, the current state does not account for all of the other sensitive applications organizations use day-to-day. This addresses only a fraction of an organization’s overall cloud footprint—and, therefore, an organization’s potential attack surface.
Solution: Visibility and Control Beyond Email, Across Cloud Applications
Through our unique, cloud-native API architecture, Abnormal is expanding coverage and protection out-of-the-box to 13 new platforms chosen based on our understanding of the threat landscape and feedback from our customers—with most of these immediately available for integration right now. These platforms include:
Salesforce (available now)
Zendesk (available now)
ServiceNow (available now)
Atlassian Jira (available now)
AWS (available now)
Azure (available now)
Google Cloud (available now)
Slack (available now)
Zoom (available now)
Workday (coming soon)
Dropbox (coming soon)
Box (coming soon)
Docusign (coming soon)
Integration takes mere minutes and is as simple as entering API information, making a few clicks, and following the detailed steps provided by Abnormal’s Data Integration Platform. The above screenshot shows how easy it is to integrate AWS into the Abnormal Portal. Once integrated, Abnormal automatically ingests activity data (including IP addresses, ASNs, VPNs, ISPs, MFA device registration, and more) from these platforms, normalizing and unifying user identities in each user’s PeopleBase profile.
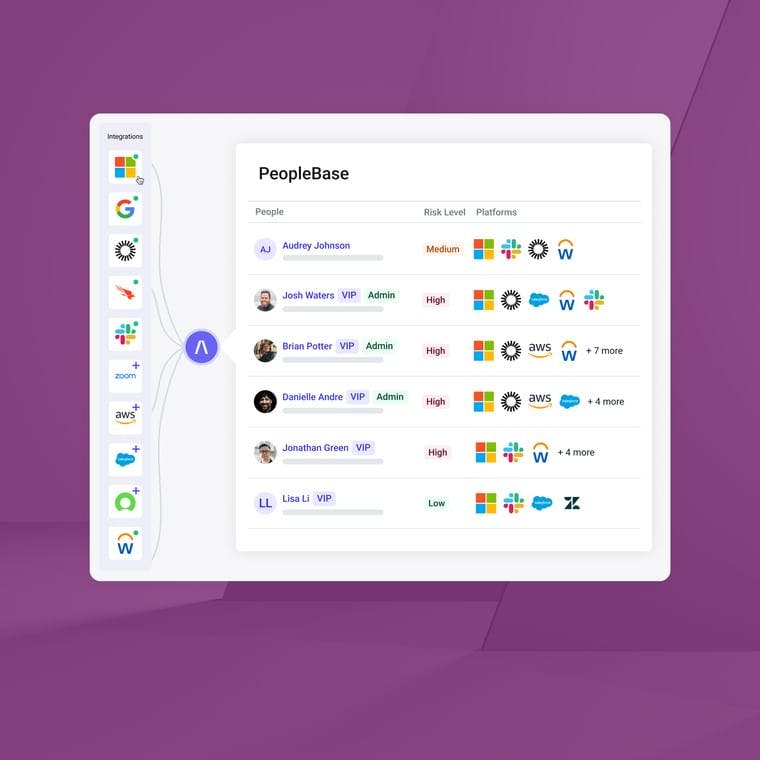
PeopleBase has also been upgraded. This database, populated with every user in your organization, has gone from an inventory of names, emails, and unusual email activity associated with each user to a comprehensive behavioral hub, monitoring and analyzing activity across your cloud ecosystem.
In the below screenshot, we see some of the key aspects of a user’s PeopleBase profile, including the Cloud Passport, which catalogs every platform to which a user is assigned, whether they have administrative access, and the date of their last sign-in. In the event of an account compromise or other threat affecting an individual or group of users, knowing what that user can access and what level of privilege they have is crucial in investigating and mitigating the impact of an attack.
Beyond the Cloud Passport, we also see the enhanced PeopleBase Notable Events timeline, highlighting unusual authentication activity across cloud applications and platforms. These timeline events not only surface suspicious activity but contextualize each event with AI insights that highlight behavioral patterns, frequencies, and potential attack tactics—once more bolstering investigatory capacity by highlighting attacker movement and likely threat groups, which can help predict an attacker’s next move.
Further, in the course of an investigation, responding to a threat can be complicated. Security teams not only need to determine the impact of the attack but must go through multiple steps to investigate cross-platform activity. As security teams often lack administrative access to many cloud and SaaS applications, it becomes necessary to involve various IT and compliance teams, open tickets, and sift through logs and unfamiliar consoles just to gather and correlate activity.
We’ve helped solve that problem as well; if a user in PeopleBase is found to be suspicious once security analysts have evaluated the user’s profile, PeopleBase can execute an Identity Disconnect*, which (depending on the actions allowed by the APIs for each integrated application) terminates user sessions and blocks account access with just the click of the “remediate” button located in the top-right corner of every PeopleBase profile.
The Value of Unified Visibility and Control
With an understanding of the problem and Abnormal’s solution, how does the value of this expansion stack up against the challenges addressed earlier? Abnormal solves them all, providing:
Superior access, visibility, and control of cloud identities, privileges, and activities that security teams must be equipped to protect
Improved efficacy not only cross-platform but cross-product by correlating against email activity and enhancing Abnormal’s AI models for better future detections
Faster incident response actions to remediate threats across platforms with a single click.
Challenge #2: Inefficient Detection and Response to Account Takeovers
While enhanced investigation through greater visibility is a huge step towards securing the cloud ecosystem, attackers have become increasingly sophisticated, and human analysis simply cannot keep pace. The cybersecurity skills gap keeps teams lean, and security leaders need a way to skill-up their employees quickly to stop the rising tide of advanced threats. How do you parse the legitimate behavioral deviations from the suspicious when you do not have enough time in the day to analyze the thousands of behavioral events occurring in the cloud? In conversations with our own customers, we’ve learned that the biggest challenges facing security teams when attempting to address this are:
Staying ahead of the increasing number of sophisticated attack tactics targeting cloud and SaaS platforms spurred on by malicious generative AI tools and as-a-service phishing kits landing in the hands of attackers
Gaining greater access and visibility into suspicious events and activities across their entire cloud and SaaS footprint to efficiently identify and respond to incidents
Finding tools that can truly stop account takeovers as current protections like MFA are being bypassed and tools meant to hunt for threats are noisy or require robust manual tuning and configuration—leaving room for human error
As mentioned earlier, Abnormal already integrates with your core cloud email and identity platforms to build comprehensive, AI-generated behavioral Cases when suspicious activity is detected—and automatically remediate the most deleterious threats. Again, though, while this has significantly improved how our customers address account takeovers (saving our customers from $329 million in potential damages in 2023 alone), that current state does not account for the other high-value SaaS and cloud targets security teams must secure.
Solution: Autonomous AI to Protect Cloud Identities
Expanding on this theme of greater visibility and control, Abnormal is announcing the Limited Release of Account Takeover Protection for all of the newly integrated applications and platforms. Account Takeover Protection delivers robust coverage and autonomous AI analysis to uniformly detect compromised users across the cloud ecosystem. Unlike current solutions that often rely on predetermined detections or customer-configured policies and rules, Abnormal automatically learns “normal” behavior and then distinguishes between legitimate and suspicious behavior.
Due to this deep AI understanding of human cloud behavior versus solely benchmarking against known attacks and indicators of compromise (IOCs), Abnormal can detect both known and undiscovered threats.
As an example, let’s start with the screenshot above of a Case involving user Brian Potter. Brian is a suspicious user detected by Abnormal’s human behavior AI engine. His first suspicious behavior was a string of 9 sign-in attempts to Okta from an IP address unused by both Brian and his organization, with 7 of the sign-in attempts failing. This is indicative of a brute-force attack, and the IP address has been associated with the Scattered Spider threat group.
You can see that Abnormal then built this behavioral Case timeline automatically, alerted Abnormal administrators to the threat, and populated the Case with cross-cloud activity spanning email platforms (with the next event after Okta being a suspicious sign-in to Microsoft 365), identity platforms, SaaS applications, and cloud infrastructure.
After accessing Okta and Microsoft 365 in the screenshots above, Abnormal continued to analyze Brian’s activity as he moved across the cloud environment.
Their next move was to authenticate into AWS, again accessing from this attacker-associated IP address, meaning Scattered Spider has moved laterally from Okta to Microsoft 365 to AWS. As security teams would typically lack real-time visibility into these movements, it’s no wonder it typically takes over 300 days on average for security teams to identify and respond to breaches due to account compromise.
Not only does Abnormal shed light on this security blindspot, but by analyzing activity across these various platforms and continually enriching Brian’s Case timeline, this increases detection confidence—reducing the risk of this simply being a false positive, avoiding the wild goose chases associated with other solutions and allowing security teams to prioritize true threats.
From here, Abnormal automatically remediated across platforms by adding Brian to CrowdStrike’s Watchlist and suspending account access across all integrated platforms. This automated remediation reduces incident response times by 10x! Further, as illustrated in the above screenshot, all Cases can also be shared with your SIEM or SOAR platform of choice to enrich your response workflows and playbooks in the wake of an incident.
The Value of Cross-Platform Unified Account Takeover Protection
Abnormal is committed to setting a new standard—simplifying security operations, preventing cross-platform account takeovers, and ensuring uniform protection across all cloud identities through the power of AI. Abnormal provides:
Extended visibility and detection using human behavior AI to autonomously identify activity tied to never-before-seen attacks
Accelerated investigation, using AI to gain greater context and visibility, reduce manual investigation efforts, and free up valuable security resources
Uniform protection for the cloud by monitoring the activity of all humans in the cloud, automatically remediating, and massively reducing incident response times
Abnormal AI Makes All the Difference
No other solution has extensive and seamless integrations atop the human behavior AI engine that allows Abnormal to quickly ingest, centralize, and consistently analyze cross-platform activity across the entire cloud environment. While many solutions will create excess noise by considering all anomalies a threat—or worse, miss zero-day attacks by comparing against a static list of known detections—Abnormal is making determinations based on a deep understanding of human cloud behavior to identify present and emerging threats.
Learn More About Visibility and Account Takeover Protection
Abnormal is changing the way organizations monitor and analyze human behavior in the cloud. Get started today by integrating your day-to-day applications into Abnormal, and join the waitlist for our expanded Account Takeover Protection coverage.
See for yourself how Abnormal AI keeps your email protected. Schedule a demo today.
*Coming in the second half of 2024
See the Abnormal Solution to the Email Security Problem
Protect your organization from the full spectrum of email attacks with Abnormal.